The evolution of Digital Transformation drives the production and use of data in businesses of all sizes and segments. Therefore, more and more businesses are looking for a Data Center provider.
The point is that the market is full of these providers and choosing the ideal partner can be a major challenge. With that in mind, we have prepared this content to help you make a secure and advantageous decision.
Below, you can learn which aspects should not be ignored before signing an agreement and choosing your Data Center. Check it out!
What is the importance of Data Center providers?
Never before has so much data been produced as today, and according to the IDC, the world will have a total of 175 Zettabytes of data by 2025. This is a reflection of the digitalization of companies, the increase in internet searches, social networks and various other common activities in the Digital Age.
With so much information available, organizations have the opportunity to turn numbers into intelligence to grow and captivate their clients. But to get there, they need the support of Data Center providers.
These partners are responsible for the secure storage, availability and connectivity of information. Without them, your business fails to take advantage of this sea of valuable data and risks falling behind the competition.
Therefore, it goes without saying that a good provider can drive business growth. After all, it provides the necessary infrastructure to implement truly strategic management, with agility and cost savings.
Checklist for choosing a Data Center provider
The Data Center is the “brain” of the company. There, you will find state-of-the-art equipment to receive, store, process and distribute the information your business needs to grow.
From storage to data processing to obtaining value and answers, everything goes through its robust IT infrastructure. In such a competitive market, you can’t really ignore its role, can you?
It is important to note that data centers have evolved with technology. That is, the companies providing these services are betting on new features to provide more agility, security and quality to their services.
But the truth is that Data Centers are not all the same! You need to make the right choice to take advantage of the best the market has to offer. Here’s what to review before choosing a Data Center!
1. Infrastructure and scalability
Data Center providers need to have a strong infrastructure, capable of scaling with business growth and offering the necessary technological support throughout the transformation journey. After all, the desire and objective of every company is to grow.
A “brain” that cannot expand is more of a hindrance than a help. Therefore, it is important to research and select a provider with the best and largest infrastructure.
These characteristics will ensure scalability to operations, with right sized resources, considering both present and especially future demands.
2. Connectivity
A Data Center without connectivity is like an island. The provider you choose needs to understand and actively work to ensure that your data is always available and can be shared in real time, wherever you are.
With today’s highly dynamic and decentralized operations, data needs to flow from one point to another. Even more so, it must be available to a wide range of stakeholders, ensuring a fast and intelligent decision-making process.
In this context, latency is also an important point, since information must be delivered in the shortest possible time.
As you are well aware, critical processes (such as financial ones) cannot suffer from bottlenecks and slowdowns. Information needs to be updated and transmitted in real time, saving you from errors and misinterpretation.
3. Credibility
The credibility of the Data Center provider is an indication of its level of quality and reliability. A growing demand has led many companies to enter the data center market, but quantity is not synonymous with quality.
Therefore, before making any decision, your company needs to take a careful look at your partner’s background, seeking someone with more experience and greater credibility. Remember that your success will depend on the efficiency and commitment of this business.
The safest decision is to team up with serious companies that possess the know-how and broad market recognition to navigate the challenges of the Digital Age.
4. Client satisfaction level
Satisfied (or dissatisfied) clients cannot be ignored. This is one of the biggest indications that the company is serious, efficient, secure and committed to the development of its clients.
Therefore, before signing an agreement, look at how the Data Center provider handles its clients and their needs. Are there complaints? Failures? How can they impact your routine?
Remember that a good partner should be accessible and interconnected with the companies that hire them. In addition, it needs to be involved with the client’s projects, assisting and seeking new solutions to optimize their processes and results.
5. Quality of support and service
The quality and agility of support and service should also be evaluated. Have you ever considered the impact of not getting an answer when you need it most?
The offer of a consultative service and focus on the client are key benefits that make the difference in the daily routine of any company. Similarly, the use of automated tools that report failures in operations to the partner is very valuable.
This not only reduces response time, but assists everyone involved in optimizing the processes, making them more stable, secure and reliable.
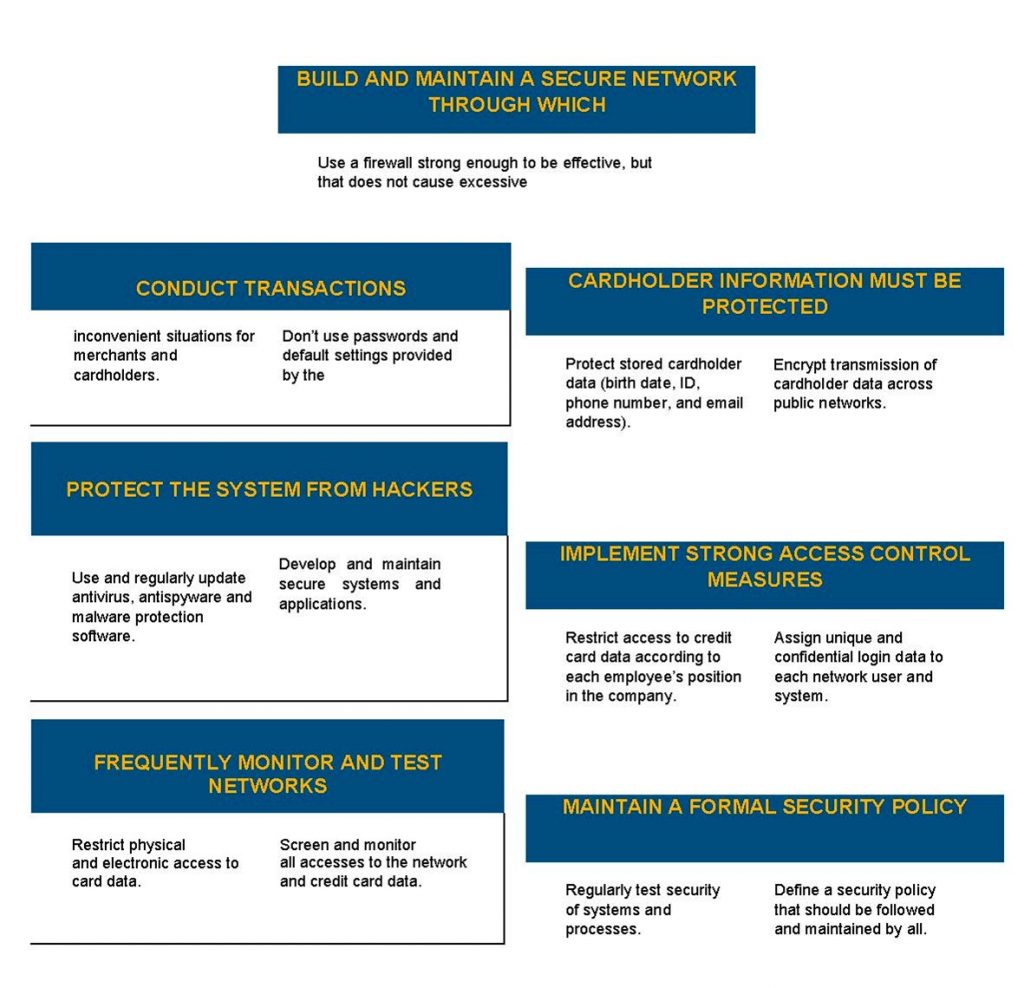
6. Security
Finally, you should evaluate the level of security offered by the Data Center provider. This is a critical point of Digital Transformation, as many cyber threats can affect data privacy and business continuity.
In this context, the choice of a partner should be based on a careful analysis of the technological infrastructure of the data environment. Key aspects include the availability of protection tools, as well as the application of security policies and good practices focused on infrastructure and people.
Remember that good partners put security first because they know the financial and reputational damage that intrusions and data leaks can entail.
The ideal Data Center provider drives your business to grow!
The evaluation of Data Center providers is one of the most important steps for the success of a business in the Digital Age. The time invested with these analyses will represent a fluid, safe operation based on the strategic use of data.
By joining forces with specialized partners, your company is much more likely to grow efficiently, overcoming the different challenges that may arise.
In addition, this is a more economical and strategic way to gain access to cutting-edge resources and policies, which would be more difficult if acting on your own and without the help of Data Center providers.
Did you like this content? Make sure to check out our post on connectivity issues and learn more!